home / public network:
IP address & mac address logged at ISP and website server you visit. ex: linux syslogs restrictions on govt blocked sites.
proxy:
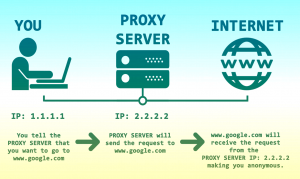
1.hide your IP
2.unblock blocked sites in your country.
3.application specific.
ex: chrome with vpn extension and skype /firefox with home network
VPN:
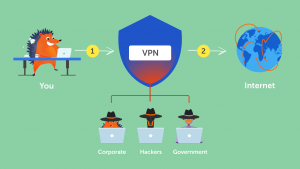
hide ip & unlock sites.
computer >>vpn >> internet (re routing slows down)
vpn companies may store data & logs,
encrypts all your network (not application specific ex: browser)
Free vs Premium VPN & Proxy
- Premium More speed & ad free traffic.
- free less speed & some ads ex: hotspot shield VPN.
Tor: dark web
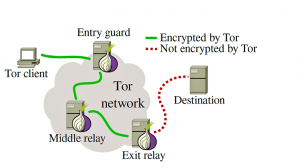
open source project by google,NSA (america.
extension with .onion
onion routing: no server use 20+ vpns
you can host & configure within your computer.
xampp to onion.
why not secure hacker injects a code in index.php once you open it automatically download into computer, do as per it programs to collect data, ex:hacking camera, reading notes, collecting browser passwords etc.
kali linux :
developed and maintained by US national security agent NSA. prest tools for hacking.
its linux based OS. linux distribution.
you can install it on linux, windows 10 using vm player, vbox etc
Pen testing: testing security rules other ways to find hack
bootforce= numerous attempts login access, server goes down,sql injection,source code injection (clean index files) etc
[INTRO] Ethical hacking / cyber Security / Penetration testing Tutorial -{updates frequently}
http vs https
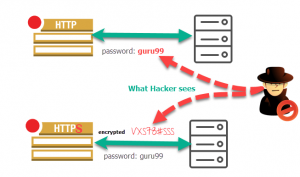
why ssl or https? to encrypt data only decrypted end user no middle man attack.
aes encryption algorithm 126,256 2mb bit more secure but big size slow speed.
4th gen supercomputer easily decrypt ssl data too.
Http protocols HTTP HTTP/2 http /3 UDP based
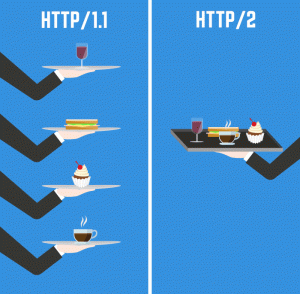
Http; every file every connection 200 connections to server for a web page 1990 still the internet (in 1990 only text now,image,video,js more files)
http2: one connection to send all files to users.
http3: maybe cross checking faster download.
How torrents works?
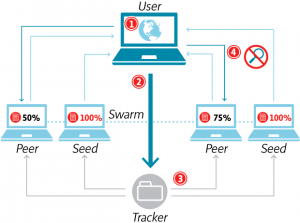
P2p (peer to peer) computer to computer no centralized server. someone share to some one downloads.
USA Arrested many people by sharing illegal files/softwares . movies on torrents.
PPTP vs. L2TP vs. OpenVPN (vpn protocols)
PPTP: weak encryption encryption and fast
L2TP :medium encryption protocols
openvpn: medium to high
you may interested in encryption algorithms.
(e.g. RSA, DSA, ECDSA) or the key exchange mechanism (e.g. DHE or ECHDE).
RSA,AES,AES-GCM/AES-CBC etc & depth of encryption measure bit 128 bit<2048<4mb bit also there for banking.
How encryption works?
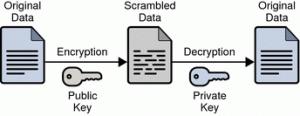
User /computer /browser: downloads public key (More Tools -> Developer tools,>> “Security” t>> “Security Overview”>> “View certificate)
server /website: holds & private key when public & private matches
SSL v3 or TLS v1.3 is still in the draft stage. google implementing sslv4 udp based more encryption & more speed.
TCP VS UDP protocols
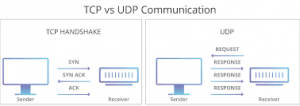
TCP: no loss of data server to user cross checks handshake slow.
UDP: faster download no /handshake crosscheck