SSL handshake time:
TTFB/latency/server response time.
TCP Connections ->keep alive
– DNS 126.09 ms
– Connect 10.97 ms
– SSL 466.75 ms 300ms,
– Send 0.04 ms
– Wait(TTFB) 1585.45 ms /200ms Google suggested up to500 no issue for dynamic sites like WordPress.
– Receive 0.05 ms
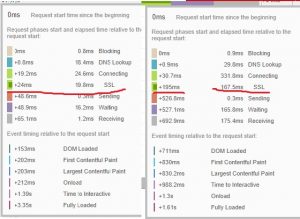
Competitor only 144ms
Fully loaded page time should be 2-3 seconds.
Page size 1-2MB.
Enable OCSP Online Certificate Status Protocol (OCSP) stapling.
eliminates the need for the client to contact the certificate authority every time, caches & stores on server for a time.
nearly 300ms to respond to a OCSP request
response on the server itself
“`
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /path/to/full_chain.pem;
resolver 8.8.8.8 8.8.4.4 valid=300s;
resolver_timeout 5s;
“`
CIPHER SUITES:
Choosing a crypto cypher that is too weak can subject your site to a number of potential vulnerabilities. On the other hand, choosing a stronger cypher can add load if your site is already CPU bound.
Rsa keys are too old but popular 2048 bit key provides 112 bits of security and 3072 bits provides 128 bit security. While ecdsa 256 bit key provides 128 bit security its enough. If you need more security inrease key bit size adds latency.
ssl_prefer_server_ciphers on | off;
Specifies that server ciphers should be preferred over client ciphers when using the SSLv3 and TLS protocols.
Turnoff ssl session tickets:
Specifices cache with session tickets. Some security issues.
Using these cipher suites(set alogrithims->key exchange,encyption, data inegryty et you are you doing to help
HTTP Strict Transport Security (HSTS):
Avoid http to https time insrucuts browser use https.
Browser directly makes connection through https, eliminates checking http.
Using latest TLS extension:
TSLS 1.2 supported by all browsers and increased performance and security.
TLS 1.3 supported by chrome, Firefox
It it in (28th) draft status from 2014.
Beta versionimplted by openssl and supports by Apache, nginx. 2x performance. By cutting ssl handshake round trips from 4-to 2.
SSLV3 and TLSV1 have security vulnerabilities they are deprecated.
SSL Session caching: enable it store sessions to to avoid extra ssl handshake for know visits/users.
Valid for 1d to 1h.
Disable session tickets
Reduce ssl buffer size to minimize ttfb
Disable old SSL.protocols
Sample ssl configuration
Redirection settings
Port
Domainname
Root directory
SSLCertificateFile /etc/apache2/ssl/godaddy.crt
SSLCertificateKeyFile /etc/apache2/ssl/new.key
SSLCACertificateFile /etc/apache2/ssl/gd_bundle-g2-g1.crt
ssl_session_cache shared:le_nginx_SSL:1m;
ssl_session_timeout 1d;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers “EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH”;
ssl_ecdh_curve secp384r1;
ssl_stapling on;
ssl_stapling_verify on;
add_header Strict-Transport-Security “max-age=15768000; includeSubdomains; preload;”;
add_header Referrer-Policy “no-referrer, strict-origin-when-cross-origin”;
add_header X-Frame-Options SAMEORIGIN;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection “1; mode=block”;